Microcorruption CTF Whitehorse Write-up
- 6 mins Summary:
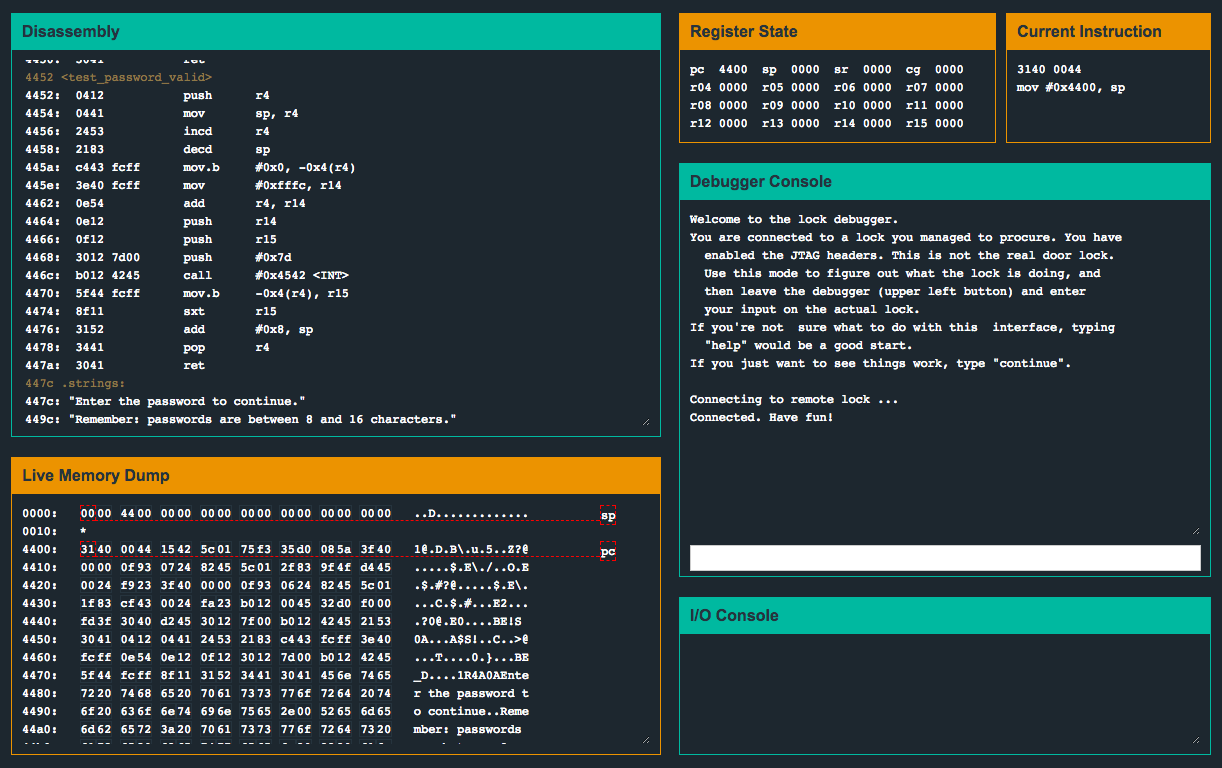
This is a write-up of my solution to the Microcorruption CTF challenge “Whitehorse” (LOCKIT PRO r c.01).
I found this challenge to be relatively straightforward and easy to solve. Let’s check out what the program is doing.
